erbbysam and I recently set out to beat the latest CTF challenge hosted by HackerOne. Here is a write-up with the process we took from start to finish.
Author: bbuerhaus
Montecrypto – ARGSS Write-Up
Montecrypto: The Bitcoin Enigma
A solve diary & challenge-by-challenge walkthrough by the crew who cracked it
ARG Solving Station: Luigy, en, JTobcat, ziot, motive, Askin, lucifers_cat
Special thanks to: Austin, nsnc, pipecork
Meet us and learn more in ARGSS https://discord.me/arg_solving_station
Escalating XSS in PhantomJS Image Rendering to SSRF/Local-File Read
I recently came across across a request on a bounty program that took user input and generated an image for you to download. After a little bit of a journey, I was able to escalate from XSS inside of an image all the way to arbitrary local-file read on the server. It's a private program, so I'm going to do my best to redact as much information as possible.
Airbnb – Web to App Phone Notification IDOR to view Everyone’s Airbnb Messages

Authors:
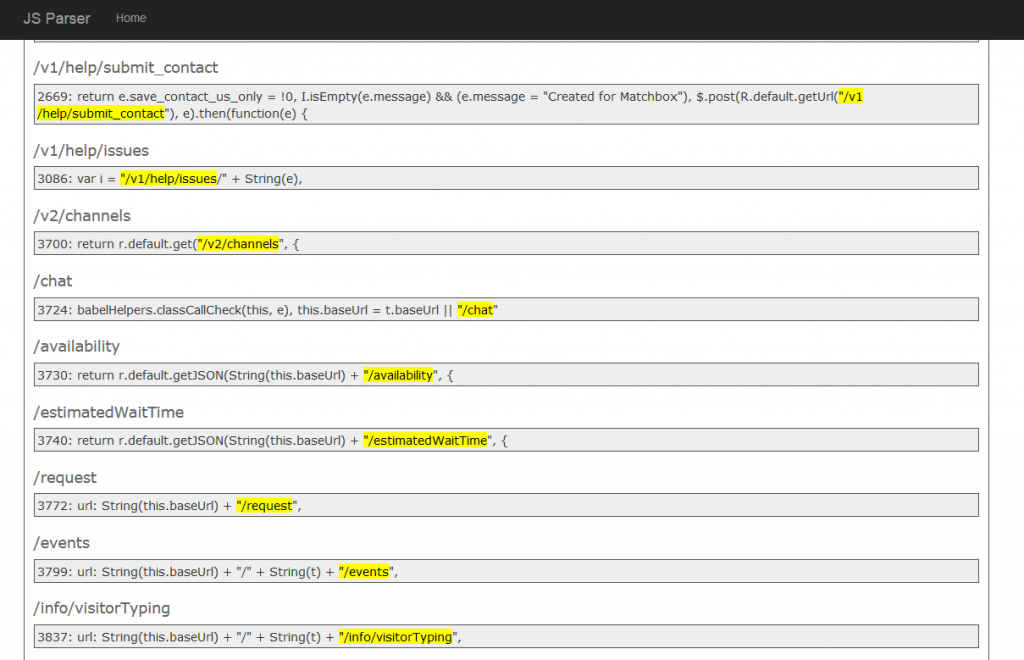
Airbnb recently created a new feature called Experiences which allows you to book things to do rather than places to stay. With the new code changes that came along with Experiences, we discovered a page that allowed you to send yourself a text message with a link to download the Airbnb app. This sent a POST request to an API endpoint we had never seen before. Using the JS Parser tool we built we discovered another API call associated with it. We found that these API calls were vulnerable to Insecure Direct Object Reference (IDOR) and allowed you to view all messages on Airbnb by ID.
Airbnb – Ruby on Rails String Interpolation led to Remote Code Execution

Authors:
@nahamsec and I discovered a Cross-Site Scripting vulnerability a few months ago related to Rails typecasting request variables into JSON. This caused the output to be JSON formatted and the JSON indexes would avoid XSS encoding. We decided to run with this concept and explore the rest of the website to see if we could identify other vulnerabilities using the same method. Along the way we discovered an interesting output from the /api/v1/listings/[id]/update API request. This led us to finding a Remote Code Execution vulnerability on Airbnb due to Ruby on Rails string interpolation.
Airbnb – Chaining Third-Party Open Redirect into Server-Side Request Forgery (SSRF) via LivePerson Chat

Update (3/15/2017):
- LivePerson reached out to me (3/9/17) after this write-up was posted and pushed out changes to patch the open redirect vulnerability. Props to their security team for following up on that!
Authors:
Ben and I spent more time on Airbnb the past few months and discovered a new endpoint that we had never seen before. After spending a year or so on the program, we were at the point of trying to find a new approach looking for vulnerabilities.
We had the idea of going through all of the js files on Airbnb looking for new endpoints. We were already doing this manually to some degree, but decided to try and automate it. So we built a new tool that grabs js files and looks for relative URLs:
Doing this we quickly found new endpoints that we had missed and found a few new vulnerabilities to report. One of the new endpoints discovered led to finding a Server-Side Request Forgery vulnerability on Airbnb.
Airbnb – When Bypassing JSON Encoding, XSS Filter, WAF, CSP, and Auditor turns into Eight Vulnerabilities

Authors:
We recently started participating in Airbnb's bounty program on HackerOne. We heard a lot about this company in the past but had never used their service before. Overall they have a pretty solid website, but we were still able to discover a handful of issues. There is one vulnerability that we wanted to write about because of the level of protection in front of it. The goal of this write-up is to show others that sometimes it takes a little bit of creativity to discover potential flaws and fully exploit them.
The vulnerability we discovered is a series of Cross-Site Scripting attacks that involved bypassing JSON encoding, an XSS filter, a pretty decent WAF, CSP rules, and eventually getting it to bypass Chrome's XSS auditor.
DEFCON 24 Badge Challenge Walkthrough

Council of 9 ventured forth to DEFCON 24 to compete in this year’s badge challenge, brought to us each year by 1o57. There was determination among the team to win at DC24 to ensure that last year’s win was not a fluke. After many sleepless nights in Vegas, we emerged victorious for a second year in a row.
Full write-up: https://web.archive.org/web/20160814065806/http://co9.io/post/148716614744/defcon-24-badge-challenge (Archive.org)
Google CTF – Web Write-Ups (11/15)

I spent some time over the weekend participating in Google's first CTF. There were 15 web challenges total with a large emphasis on Cross-Site Scripting and a few related to Google tech/products. I put together some write-ups on the challenges I was able to solve.
Google CTF – Web 7 – Spotted Quoll
Google CTF - Web 7 - Spotted Quoll