I discovered a vulnerability on Facebook that allowed you to send notifications to any user on Facebook. This could have been used to spam any content you wanted to all users on Facebook.
On the Facebook Group pages, when you add a new user to your group it creates a news post saying they have been added to the group. It also creates a group notification saying they were invited. When you "like" the group notification, it passes the Facebook user ID (uid) in a variable called user_id. Normally any request with a Facebook uid is validated to see if you are able to interact with the user. In this specific request, it only checks to see if the user exists in the database. This allowed you to interact with any user, including users outside of the whitehat sandbox.
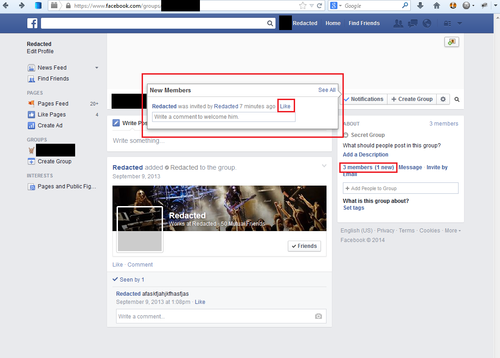
When you click the "Like" link in the Flyout pop-up, you send a special request that was built for this page. When I find one-off requests like this, I noticed that they are usually more likely to be vulnerable. It tends to be code that does not receive a lot of attention from either the hackers or developers.
The Request
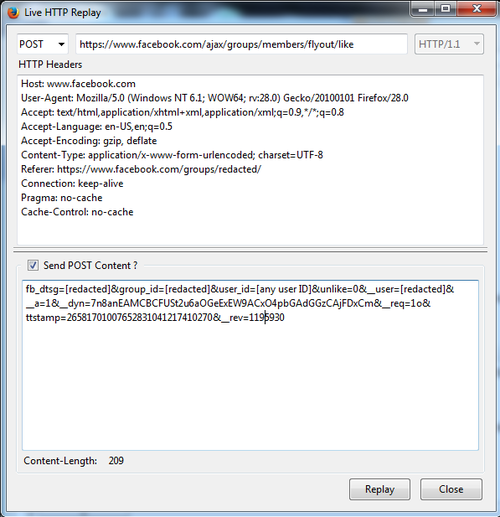
This is what the request looks like. Sometimes an exploit is simple, but it takes time to discover and understand the logic or flow of a big website.
In the first image, you can see an example of a user joining the group. As stated earlier, when you invite a user to the group and they join, it creates one of these posts. When someone comments or likes the group notification regarding the post, the user who joined is notified. When that notification is clicked, it loads the post on the group page. So the question is why does it pass user_id if it's referencing a news post and what happens if you pass a user_id that isn't in the group?
When you submit any user_id, you force create a post showing that user has been invited to the group. This is not a horrible exploit as it is only visual and it does not force the user to actually join the group. This is only the root cause of the bug, not the security vulnerability.
The problem comes from interacting with the newly created post. When you comment or like the post, the user will receive a notification. This is due to Facebook forcing that user to follow the group post that was created for them.
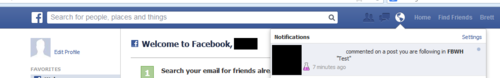
Example of a sandbox user receiving a fabricated group post notification from the live Facebook environment.
This could easily have been used to spam notifications to every single Facebook user. An example would be spreading a malicious website or message to millions of people.
The Logic
In order to properly test this, I had to create a sandbox Whitehat account and a new account on the live environment for Facebook. I setup the live environment account to have the strictest privacy settings so that it should be impossible for anyone to search for that user or invite them to a group.
While testing, I tried both of the user IDs in the flyout/like request and they were both notified of comments on the post of them joining the group. When trying an invalid user ID, it would fail. So it is likely that their Facebook Query Language (FQL) query is checking if the user exists without any additional privacy checks.
My guess on the logic of this flow:
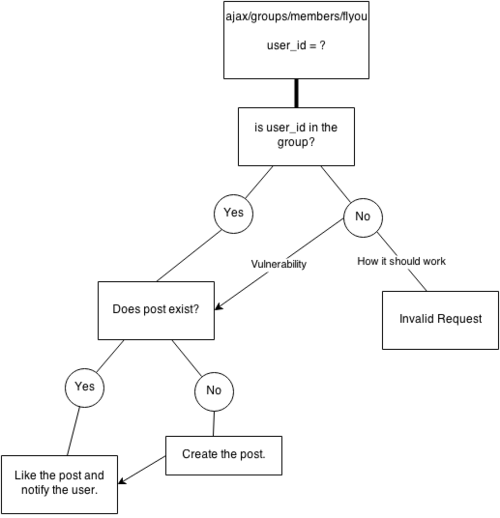
I'm sure there is more to it than this, but this will give you an idea of how I perceived the exploit based on my interaction with the request alone.
The Solution
The group notification should have a post associated with it rather than a user_id. If you like or comment the notification, it should interact with the group news post directly. If not this, it should validate that the user has actually been invited or is part of the group before creating the post.
The Bug
- Bug submission: August 2013
- Bug fixed and paid out: February 2014
