Google CTF - Web 4 - Dancing Dingoes
Description: "We're interested in finding out what information is stored on this website. We've already obtained the username "proff" and the password "strobe.c", but can't work out how to access the "admin" user. Any ideas?"
The only thing we have when we load this website is a login form. We are given a login (proff/strobe.c) in the challenge description. When we log into the site, we are given a list of documents of no importance. Going back to the login, I monitor the requests that I send when I log into the website.
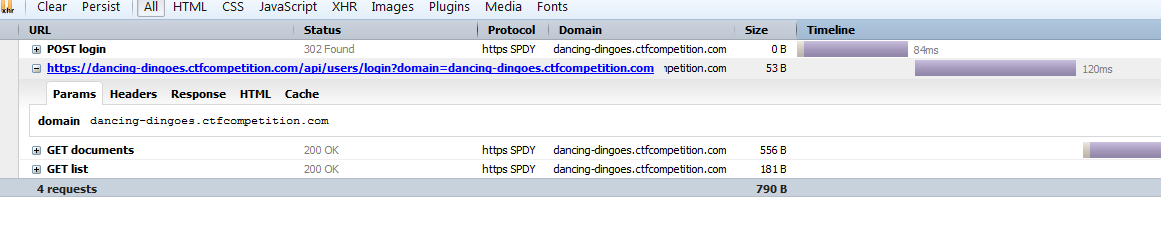
There's a strange /api/users/login endpoint request that includes a suspicious domain GET request variable. I decided to throw a random fuzz character (') into it to see what the response is.
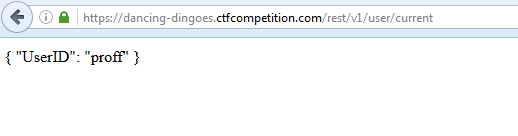
As you can see in the error response back, it's trying to load https://[domain]/rest/v1/user/current. I load the endpoint to see what the server is processing.
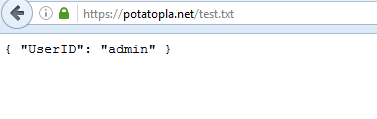
Ok, it's specifying that the current user is "proff", the user that I logged into. Because we are able to specify the domain, I create a txt file on my web server and change "proff" to "admin".
Now we load the following URL:
https://dancing-dingoes.ctfcompetition.com/api/users/login?domain=potatopla.net/test.txt?
We are redirected to the following:
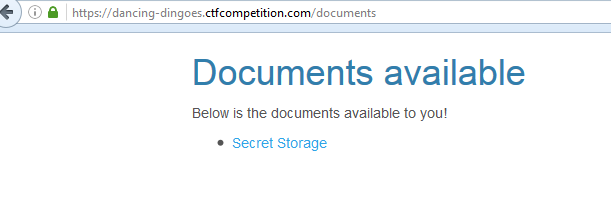
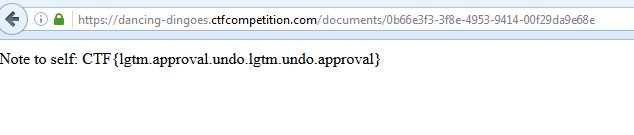
We can see that admin was the right user and we now have a new document.
Loading the document: