I recently started to review the automated vulnerability scanner Burp Suite because of its widespread usage. The tool is used by many security bounty hunters, security professionals, and blackhat hackers for automated scanning and vulnerability detection. While I was using Burp, I was wondering to myself how easy it is for a server to detect that I am using this tool.
Burp Suite
This is a description of Burp Suite as found on their website:
Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application's attack surface, through to finding and exploiting security vulnerabilities.
How it Works
Burp Suite works by sitting between your browser and the internet. All of the requests sent by your browser are going through a proxy that is relaying all of the requests and response information to Burp.
Web Proxy
While using the tool, I noticed there is a feature that hosts an intranet server on your machine. By default this website sits on http://127.0.0.1:8080 and is also accessible at http://burp.
This service exists because there are many times when you want to send a request discovered or logged by Burp tool in your browser. When you select that you want to repeat or copy the request, it'll create a URI endpoint in order to fabricate the request. The reason it does this instead of just copying the URL is because of the additional information requested by POST requests.
Actions:
- Proxy History: http://burp/history
- View History by ID: http://burp/orig/1
- Repeat Request on View History (form, no URI)
- Show Response on View History (form, no URI)
- Repeat Request by ID: http://burp/repeat/1
- Show Response by ID: http://burp/show/1
The actions we are interested in are the ones that have an html form and a forced redirect.
Repeat Request by ID
A user has to manually click "Request in Browser" inside of a context menu inside of Burp Suite. I would imagine this feature is not used as commonly as the scanner/spider. Even still, someone using this feature is probably a little more technically minded and digging deeper into your website than just the scanner.
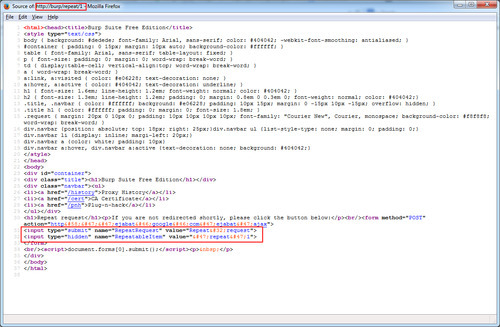
Screenshot of the internal page source:
Screenshot of the requests:
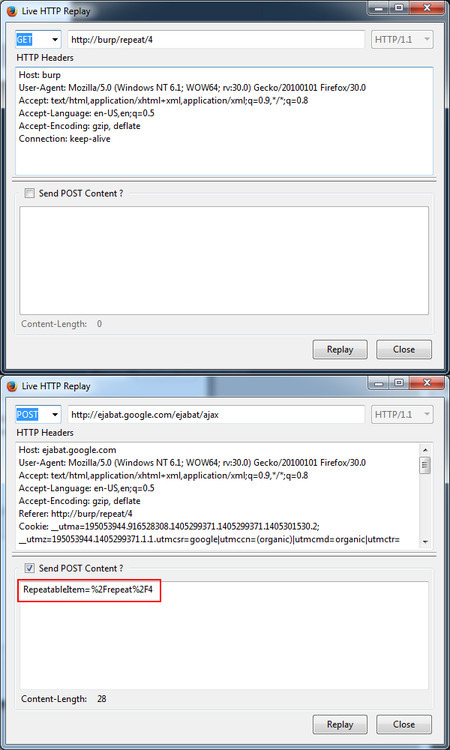
The page is using JavaScript to force the form to execute in your browser to execute an automatic POST request. There are hidden and submit inputs that are not typically part requests sent and are unnecessary. You can look for these request variables inside of your network traffic logs or have your WAF pick up on them to flag or scrutinize traffic from that IP.
POST Request Variables to look for:
- RepeatableItem=/repeat/[id]
- RepeatRequest=Repeat+request
- ViewResponse=Show+response
- RenderableItem= /show/[id]
Detection
This is not complete detection and most people who use Burp Suite do not use the web proxy features. At the very least, this is data that you can search for in your traffic history. You could also plug into your WAF to see what vulnerabilities Burp has discovered.
Part 1 of 3
This is part one of a three part series:
- Part 1: Info Leak
- Part 2: Callback Exposure
- Part 3: Traffic Heuristics and Honeypots