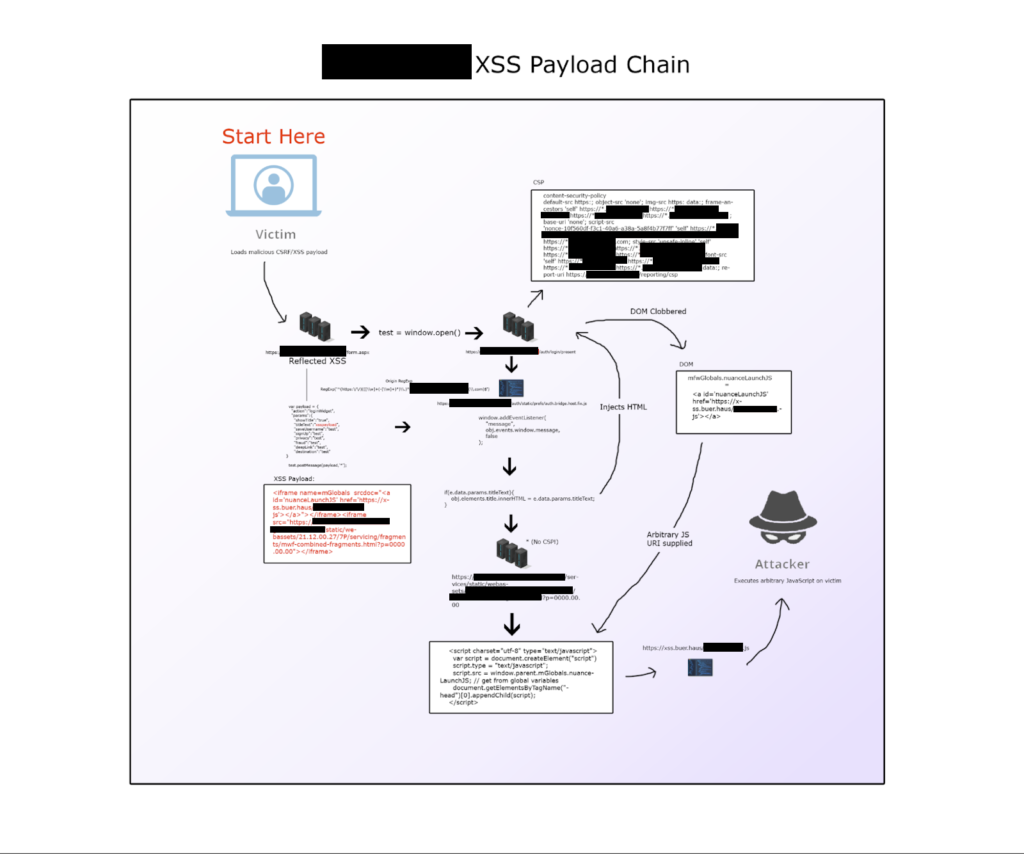
A few years ago, I discovered a Cross-Site Scripting (XSS) chain that incorporated several interesting methods that I usually see in write-ups or Capture the Flag challenges. I had to heavily redact this blog post to ensure the anonymity of the company because it is a bug bounty program with a no disclosure policy. In this post you will see the story of the initial discovery, roadblocks, and finding ways to continue increasing impact to achieve our goal.
Security
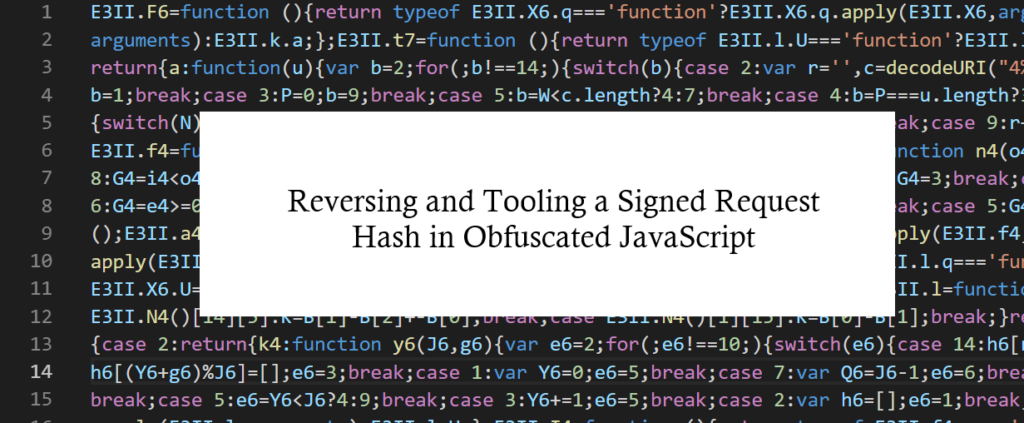
Reversing and Tooling a Signed Request Hash in Obfuscated JavaScript

DEFCON 29 CTF Qualifier: 3FACTOOORX Write-up
I recently participated with the CTF team Norse Code representing Hacking for Soju in the DEFCON 29 CTF qualifiers. There was a web challenge, so I went full speed ahead to solve it. Overall the challenge is fairly straightforward and not too difficult, but I decided to do a write-up on it to demonstrate one way that you are able to work through obfuscated JavaScript.
The challenge begins with a website link and a Chrome browser extension that you can download.
h@cktivitycon – Pizza Time (Web 750)
HackerOne just ran the online h@cktivity con and with it was a CTF. I spent 15 hours solving the big web challenge with the team Hacking for Soju called Pizza Time! This is yet another solid web CTF challenge created by the wizard Adam Langley.
This is the challenge text that leads you into it:
NahamCon – Trash the Cache Write-up (Web 1000)
I recently participated in the NahamCon CTF with the team Hacking for Soju. I was unable to complete this challenge before the end of the CTF, but managed to solve it the following day. Credits to maneolt and xehle for sharing notes and giving me a couple nudges.
Shout-out to the challenge creator Adam Langley (give him a follow) for keeping the hype going after the CTF ended and also making one of the better web CTFs I have seen!
It starts with Hackbookagram.com
A Tale of Exploitation in Spreadsheet File Conversions
Researchers:
Statement from Slack
Slack would like to thank the researchers for their work to increase the security of the open source tool LibreOffice and their responsible disclosure to Slack. The security of file sharing is critically important to Slack and its users, and we worked with the research team to quickly implement a fix within 24 hours of receiving the report. Slack has confirmed that no customer data was accessed using this bug.
Intro
In our attempt to fingerprint LibreOffice as a PDF rendering service, we identified multiple implementation vulnerabilities.
This writeup covers our efforts to fingerprint LibreOffice, LibreOffice file detection (and abuse) & misuse of the LibreOffice Python-UNO bridge.
The unintended misuse of the Python-UNO bridge by the popular package unoconv resulted in CVE-2019-17400.
We believe our research here is not final, and encourage others to look into this area.
H1-5411 CTF Write-up by erbbysam and ziot
erbbysam and I recently set out to beat the latest CTF challenge hosted by HackerOne. Here is a write-up with the process we took from start to finish.
Escalating XSS in PhantomJS Image Rendering to SSRF/Local-File Read
I recently came across across a request on a bounty program that took user input and generated an image for you to download. After a little bit of a journey, I was able to escalate from XSS inside of an image all the way to arbitrary local-file read on the server. It's a private program, so I'm going to do my best to redact as much information as possible.
Airbnb – Web to App Phone Notification IDOR to view Everyone’s Airbnb Messages

Authors:
Airbnb recently created a new feature called Experiences which allows you to book things to do rather than places to stay. With the new code changes that came along with Experiences, we discovered a page that allowed you to send yourself a text message with a link to download the Airbnb app. This sent a POST request to an API endpoint we had never seen before. Using the JS Parser tool we built we discovered another API call associated with it. We found that these API calls were vulnerable to Insecure Direct Object Reference (IDOR) and allowed you to view all messages on Airbnb by ID.
Airbnb – Ruby on Rails String Interpolation led to Remote Code Execution

Authors:
@nahamsec and I discovered a Cross-Site Scripting vulnerability a few months ago related to Rails typecasting request variables into JSON. This caused the output to be JSON formatted and the JSON indexes would avoid XSS encoding. We decided to run with this concept and explore the rest of the website to see if we could identify other vulnerabilities using the same method. Along the way we discovered an interesting output from the /api/v1/listings/[id]/update API request. This led us to finding a Remote Code Execution vulnerability on Airbnb due to Ruby on Rails string interpolation.